PwC: Does procurement understand third party cyber risk?

“You can’t secure what you can’t see,” said PwC. According to the consultant’s ‘2022 Global Digital Trust Insights Survey’, most organisations are facing challenges when it comes to their third party risks, due to the complexity of their business partnerships and supplier networks.
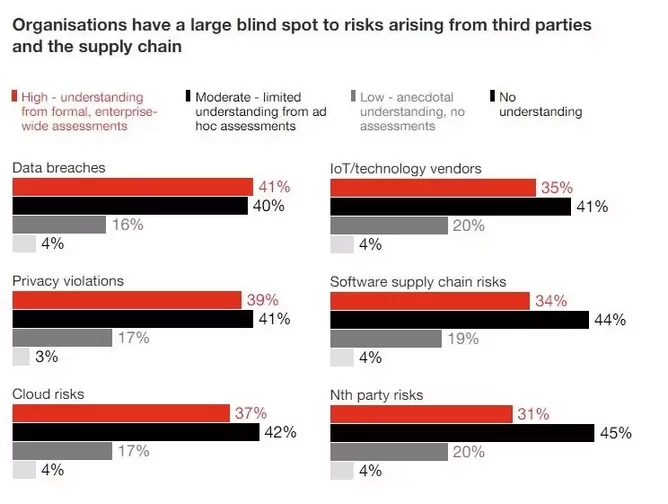
It is important to understand the severity and the lengths that cyber attackers are willing to go, With only 40% of organisations thoroughly understanding the risks of data breaches through third parties, and nearly 25% having little or no understanding many organisations risk exposing a major blindspot within their organisations prime for cyber attackers to exploit.
The rise in third party cyber attacks in procurement and supply chain
Among PwC’s respondents, 56% are expecting an increase in reportable incidents in 2022 relating to attacks on the software supply chain. Despite this, only 34% have formally assessed their exposure to this risk. Similarly, 57% expect a jump in attacks on cloud services, but only 37% understand cloud risks.
“The ‘most improved’ organisations, on the other hand, have taken note and taken action. They are 11x more likely to report a high understanding of their third-party risks. [75%] say they’re highly knowledgeable about third-party dangers in five of six areas,” said PwC.
“Only in their knowledge of ‘nth-party’ risks — those posed by their suppliers’ suppliers and so on, down the line — does the number dip: 69% of the “most improved,” 31% for the rest. The more complex the connection, the harder it becomes to see the risks buried within.”
Despite understanding the escalating threat due to complex business ecosystems, only 30% to 46% of organisations are responding to the escalation. “The ones that have responded seem to be focusing their efforts primarily on today, perhaps at the expense of tomorrow,” commented PwC.
So how are organisations currently minimising third party risks?
- 46% auditing or verifying supplier compliance
- 42% sharing information with third parties or helping to improve their cyber stance
- 40% addressing cost or time-related challenges
PwC commented that while organisations are making some efforts to minimise risks, the above are mostly reactionary solutions, PwC only considers one response to be proactive - refining criteria for onboarding and ongoing assessments (42%) - which the consultant found publicly listed organisations are more likely to make (47%).
“Still, more than [50%] have taken no actions that promise a more lasting impact on their third-party risk management,” said PwC. 58% of organisations are yet to refine their third party criteria, 60% haven’t rewritten contracts, and 62% haven’t increased their due diligence, while ‘most improved’ organisations are five times more likely to have taken all seven of the above actions.

Simplifying procurement and the supply chain
“Today’s trending cyber-attack target may be the most nefarious one yet: your supply chain of trusted vendors, suppliers and contractors. The weapon? A process many have taken completely for granted: the software update. The payoff? Ransom payments to cybercriminals, valuable intelligence to nation-states or training data sets for AI models to competitors,” commented PwC.
According to the Atlantic Council, vendors and hijacked updates have accounted for 60% of software supply chain attacks over the past decade, with predictions from the European Union Agency for Cybersecurity (ENISA) expecting 2021’s supply chain attacks to have quadrupled compared to 2020.
While an organisation’s own cyber defences could be good, organisations can still be vulnerable to supply chain attacks through their suppliers. Software-based attacks can be difficult and complex to unravel in the supply chain due to the integrated dependency of one component on another.
“The organisations that had the best cyber outcomes over the past two years have consolidated tech vendors as a simplification move. Paring the number of tech and other third parties reduces complexity and increases your ability to know how secure they are,” said PwC.
By simplifying operations, multiple functions including procurement, risk managers, fraud team, legal, and security can better understand their roles in protecting the supply chain from cyber attacks.
“Gaining visibility into the web of third-party relationships and dependencies is a must,” commented PwC. “Top cybersecurity companies integrate solutions (real-time threat intelligence, threat hunting, security analytics, vulnerability management, intrusion detection and response) on broad platforms.”
PwC also found that those with more advanced data trust practices, “significantly reduced their number of third-party relationships, increased their monitoring, deepened their assessments of third parties and felt confident that their third-party risk management program had shown tangible benefits in the last two years.”
To find out more, read PwC’s 2022 Global Digital Trust Insights Survey.






